How often is the DNS HTTPS record used?
Specifically, how many websites have it present? I wrote a few crude Python scripts to gather that data for me.
TLDR: About 24.2% of the most popular websites have a HTTPS record. The least used record parameter is “port” (<0.01%), followed by “ech” (~67% of sites with HTTPS set). Data
What is HTTPS?
Not to be confused with the protocol, the HTTPS record is part of the Service Binding spec. Frankly, I have no idea how any of it actually works, but all you need to know for this post is that it lets clients get extra info, such as supported HTTPS protocols and IPs, with less DNS requests and before actually connecting to the website.
; <<>> DiG 9.18.36 <<>> @8.8.8.8 cloudflare.com HTTPS
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 49755
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;cloudflare.com. IN HTTPS
;; ANSWER SECTION:
cloudflare.com. 300 IN HTTPS 1 . alpn="h3,h2" ipv4hint=104.16.132.229,104.16.133.229 ipv6hint=2606:4700::6810:84e5,2606:4700::6810:85e5Receiving this data upfront can reduce TTL.
There are a few supported fields for the HTTPS record:
alpn, lists supported protocolsipv4hintandipv6hintlists IP addresses to avoid having to make more queries for themport: rarely used for HTTPS, indicates what port to connect toech: Encrypted Client Hello, which I’ll talk about in the following sections.
Why do I care?
I originally intended to only study the adoption rate of Encrypted ClientHello, as I’ve been researching its applications.
Encrypted ClientHello reduces the amount of information that’s sent unencrypted about which websites you visit. Every time your browser connects to a website over TLS, it sends in its initial handshake request (the ClientHello) the domain that it’s trying to reach, via the SNI extension.
This can be a problem in some situations. For example, even though many browsers support encrypted DNS over HTTPS, your ISP will still be able to track which websites you’re visiting through deep packet inspection, as the domain name is sent in plaintext at the start of a TLS connection.
Encrypted ClientHello aims to solve that by fetching encryption configs from secure DNS and using it to encapsulate the ClientHello. This hides which specific domain you’re trying to visit, improving privacy. This config is stored in the HTTPS record, which is why I wanted to take a look at it.
At some point, I thought it’d be neat to also include how often other fields show up and what CDN each website uses.
Methodology and limitations
I used the Tranco list as input for my processing. It merges various site rankings into one big list. To do the querying, I wrote a quick and dirty Python script that resolved the domains via Google Public DNS.
I did this all on my PC with a mildly unstable internet connection, so some queries timed out and had to be excluded. Other domains had nameservers that rejected HTTPS queries, so those were also filtered out. Most (94.9%) were resolved fine, so I don’t think it’s that big of a deal.
While I was writing this post, I noticed my HTTPS record usage data doesn’t match what Cloudflare Radar reports. I’m not really sure why, but to my knowledge it isn’t my querying script. It might be because I’m sampling a relatively tiny part of the Internet.
The Data
Yes, Finally, I’m getting to it.
Query success rate:
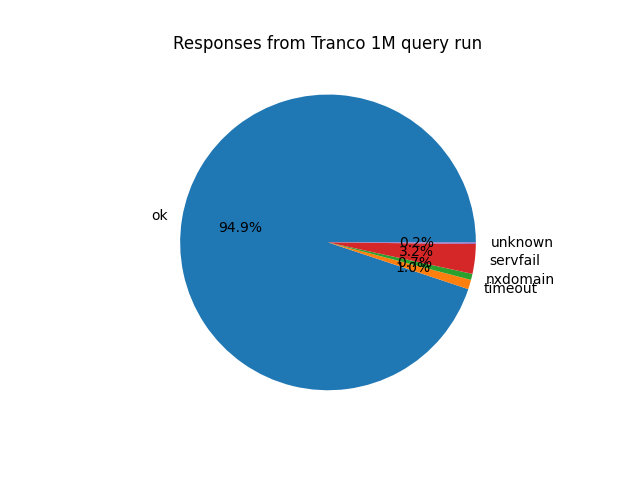
- 948810 successful queries, 51190 failures
- 10357 timeouts
- 6672 NXDOMAINs
- 32497 SERVFAILs
- 1664 other unknown errors
If I did this on a VPS, these numbers might’ve been better. 95% out of 1 million still sounds good to me, though.
% of domains with HTTPS record:
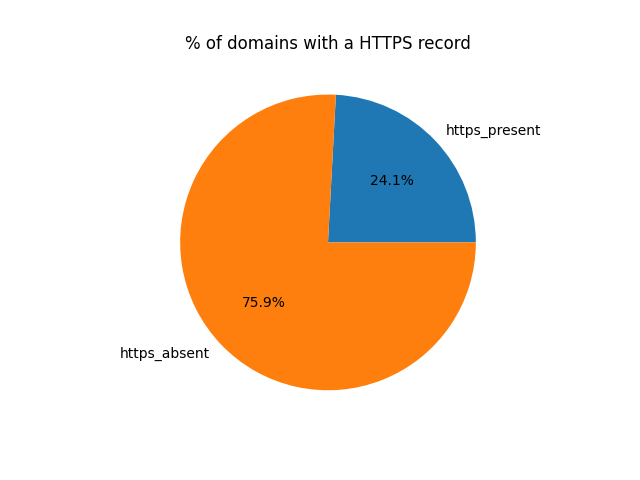
- 229124 domains with HTTPS record
- 719686 domains without
Usage of HTTPS record fields (out of all HTTPS record domains):
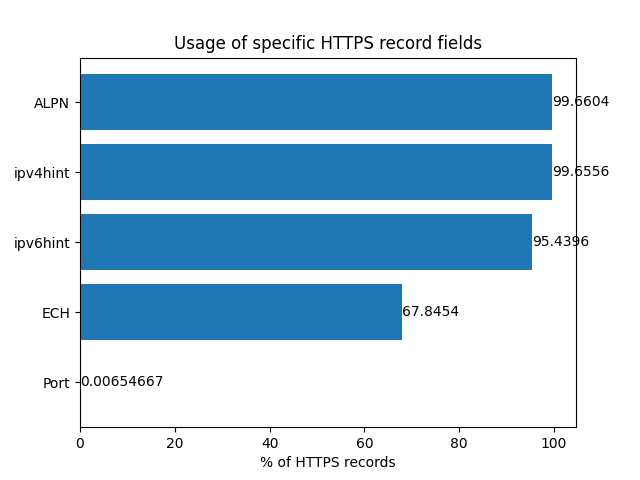
- 228346 domains with
alpn= - 228335 domains with
ipv4hint= - 218675 domains with
ipv6hint= - 155450 domains with
ech= - 15 domains with
port=
The ALPN and IP hints are by far the most common, as they give the highest benefits (aka faster connections) for how easy they are to set up.
ECH is lagging behind the rest in this chart, though its usage is still a surprise for me. I’ve heard barely anything about ECH outside of Cloudflare’s blog, so I assumed no one enabled it because no one cared enough. I expected it to be around 10 to 20%.
Only 15 domains used the port field. The only port used was 443:
airnewzealand.co.nz
dnshome.de
airnewzealand.com
airnz.co.nz
airpointsstore.co.nz
airnewzealand.com.au
nethorizon.pl
airnz.com
untarget.ai
christchurchcasino.com
planaltonet.net.br
managed.fi
airnewzealandcargo.com
datamagic.at
airnewzealand.jpUsage of HTTPS record fields (out of all domains):
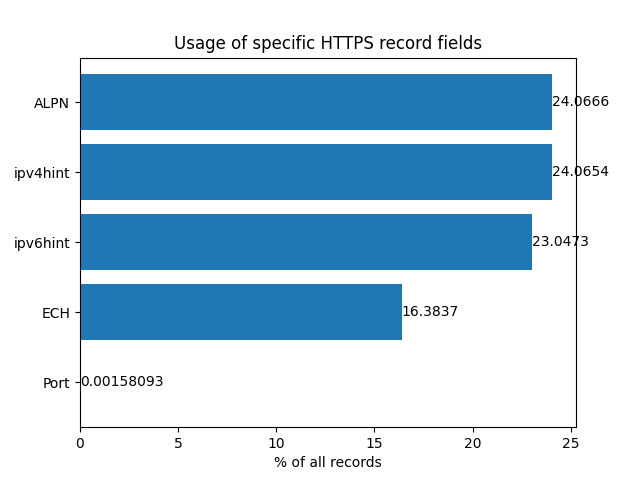
ECH-enabled websites still make up only a small fraction of the most popular websites, though.
% of domains with HTTPS record (by CDN):
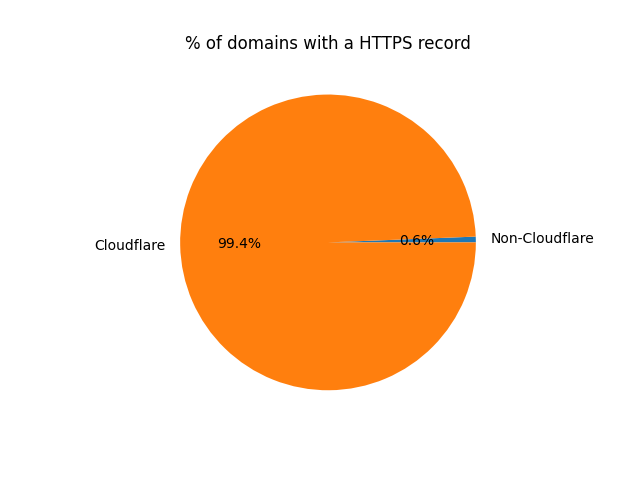
- 227689 domains that are likely behind Cloudflare
- 646 domains that likely aren’t
I say “likely” because I used the ipv4hints as an indicator. Cloudflare doesn’t publish all their IP ranges, only the ones used to make proxy requests, so I had to use this list.
Nearly all domains with HTTPS configured are behind Cloudflare. This is because Cloudflare creates those records by default for all domains that have proxying enabled.
% of domains with ECH configured (by CDN):
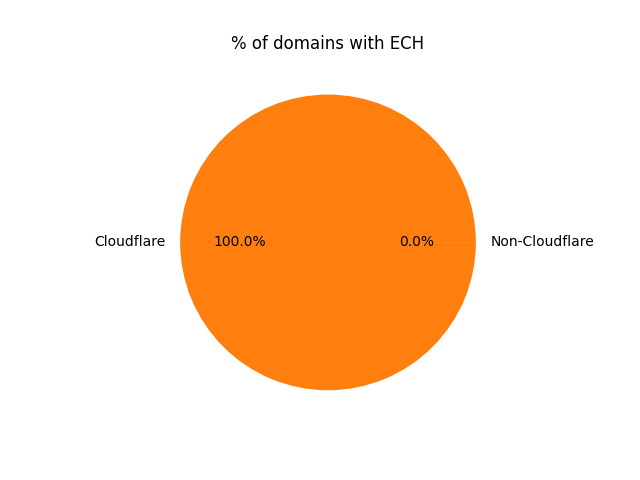
- 155434 ECH-capable domains are likely behind Cloudflare
- 16 ECH-capable domains likely aren’t behind Cloudflare
The amount of non-CF ECH-capable websites is literally a rounding error. This clearly illustrates one of the biggest issues with ECH: centralization.
The upside is that all ECH traffic looks like it’s accessing one single website, cloudflare-ech.com, instead of the actual domain names. In other words, the anonymity set of ECH is widened.
The downside is that all ECH traffic depends on Cloudflare, which isn’t great for a variety of reasons.
These are the domains that aren’t using Cloudflare, and have instead deployed their own ECH. WARNING!!! Some of these websites contain NSFW content!
| Domain | Host | Outer SNI |
|---|---|---|
| strip2[.]club | AS58061, Scalaxy B.V. | usuarioporno[.]com |
| strip2[.]co | AS58061, Scalaxy B.V. | usuarioporno[.]com |
| dweb[.]link | AS40680, Protocol Labs | cloudflare-ech[.]com |
| strip2[.]in | AS58061, Scalaxy B.V. | pornhub[.]com |
| spaces[.]im | AS58061, Scalaxy B.V. | spaces-games[.]com |
| modelcontextprotocol[.]io | AS399358, Anthropic, PBC | cloudflare-ech[.]com |
| usersporn[.]com | AS58061, Scalaxy B.V. | pornhub[.]com |
| spaces[.]ru | AS58061, Scalaxy B.V. | world79[.]spcs[.]bio |
| makenotion[.]com | AS33191, Notion Labs, Inc. | cloudflare-ech[.]com |
| kinotam[.]pro | AS58061, Scalaxy B.V. | world79[.]spcs[.]bio |
| gdespaces[.]net | AS58061, Scalaxy B.V. | world79[.]spcs[.]bio |
| kinotam[.]org | AS58061, Scalaxy B.V. | world79[.]spcs[.]bio |
| hided[.]net | AS4766, Korea Telecom | ech[.]example[.]net |
| lucky666[.]cn | AS55933, Cloudie Limited | ech_speedtest[.]lucky666[.]cn |
| mypodseurope[.]io | AS24940, Hetzner Online GmbH | google[.]com |
| ewpratten[.]com | AS54041, Evan Warren Pratten, Sole Propietorship | cloudflare-ech[.]com |
Conclusions
ECH adoption is very low
And I think that’s because of how hard it is to set up. You need to build your own Apache and nginx server from forks that are slightly out of date, somehow generate the correct ECH config to put in the HTTPS DNS record and test if:
- ECH is even being used (to make the maintenance worth it), and
- ECH doesn’t break some ancient clients
Or you can use Cloudflare. Then you’ll get easy ECH, but your website will go down when the inevitable Cloudflare outage happens, as well as the usual privacy concerns.
I know of only one web server that supports ECH natively: Caddy. However, the public domain used in the outer ClientHello must be one that you own, as it will be used as a fallback, ensuring the server name is protected even when clients can’t obtain ECH configs for whatever reason. It unfortunately means you can’t set the outer SNI to a random domain.
The HTTPS record isn’t that popular either
This time, I think it’s less about difficulty and more that webmasters forget this record even exists.
Air New Zealand is the biggest user of the port= field
That’s weird.